- Published on
How to Setup VPC Peering on AWS
- Authors

- Name
- Ruan Bekker
- @ruanbekker
In this tutorial I will demonstrate how to create a VPC Peering Connection between Two AWS Accounts and how to route traffic between them and then show you how we create Two EC2 Instances and demonstrate how to SSH to each other via it's Private IP Address.
Scenario Information
We will have Two AWS Accounts in this demonstration, a "Green AWS Account" and a "Blue AWS Account".
In this scenario, we will have two teams, both teams manage their own account and in this scenario the two teams need to be able to communicate to each other. To keep it simple, each team has a EC2 instance and the two EC2 instances need to be able to communicate with each other.
Therefore we will setup a VPC Peering Connection between the two accounts. Both accounts will be operating in the eu-west-2 (London) region.
Account, CIDR
green: 10.1.0.0/16
blue: 10.2.0.0/16
Getting Started
This will be our Green AWS Account:
This will be our Blue AWS Account:
Creating the VPCs
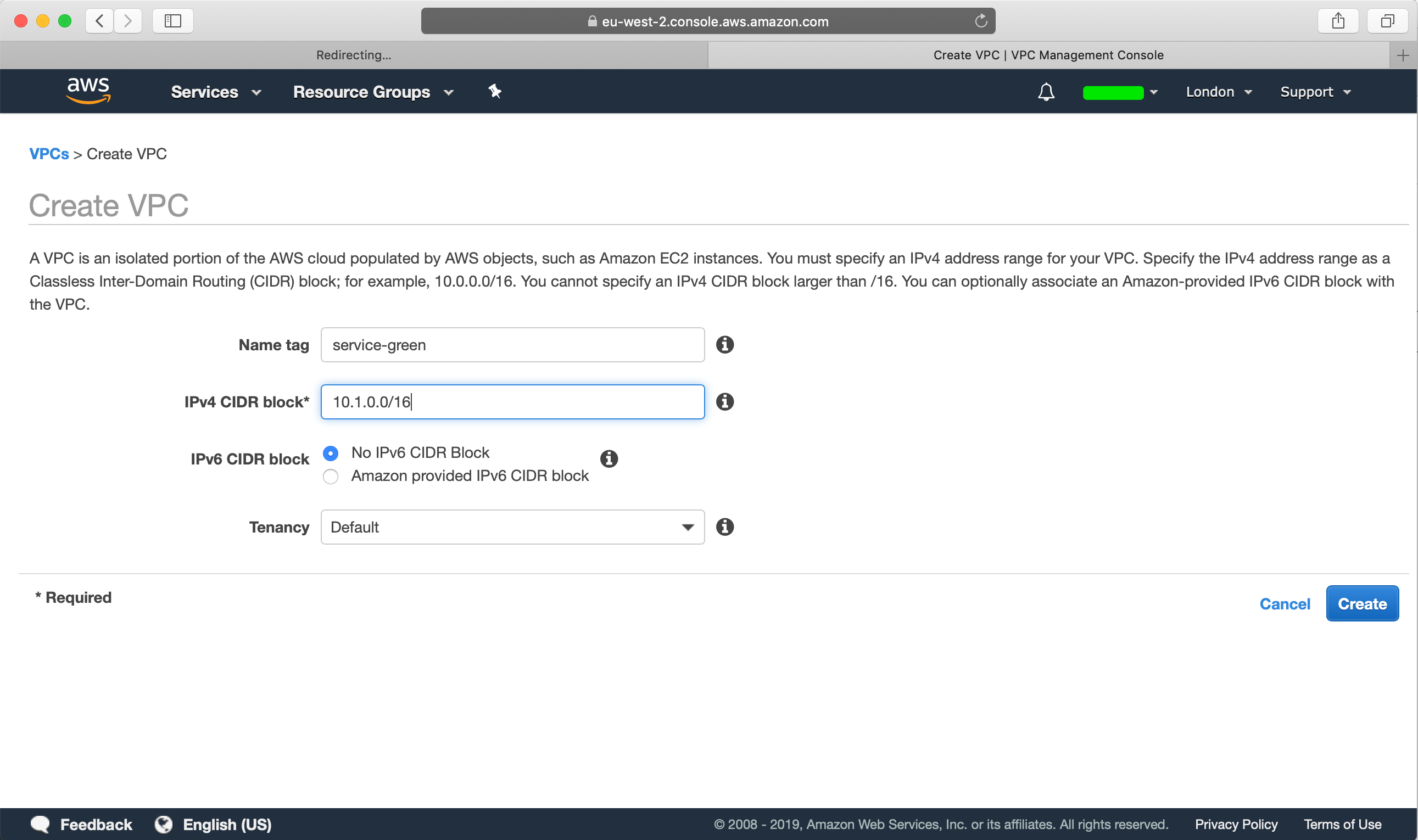
From our green account, head over to VPC and create a new VPC with a CIDR of 10.1.0.0/16:
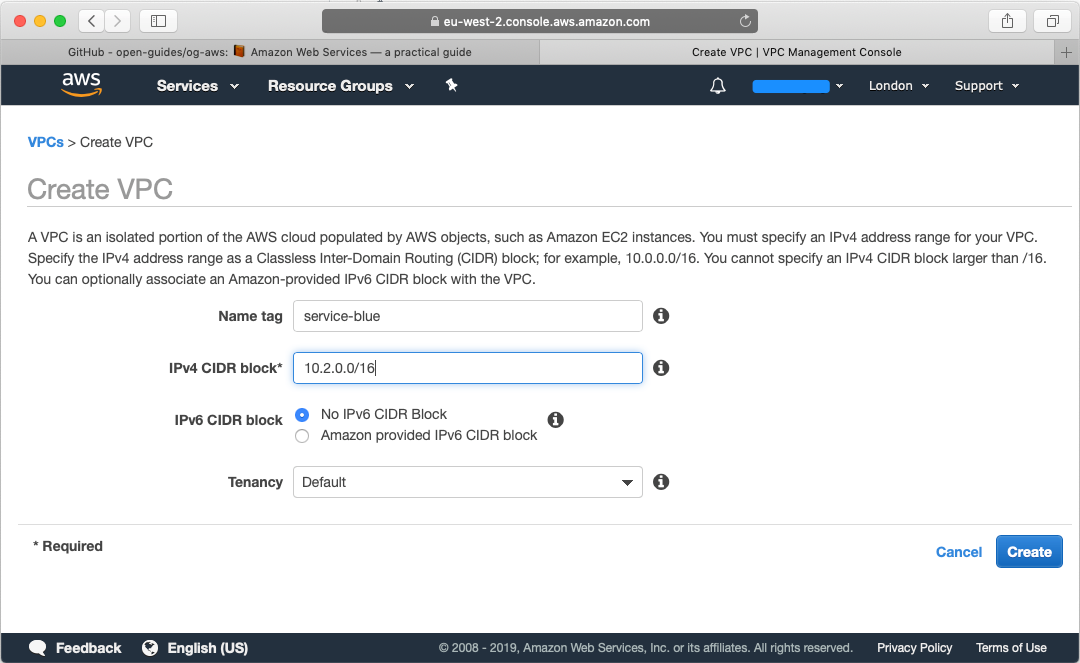
Then head over to the blue account, head over to VPC and create a new VPC with CIDR of 10.2.0.0/16:
So in summary we have the following resources:
Green: vpc-0af4b247a1353b78b | 10.1.0.0/16
Blue: vpc-031c4ce3f56660c30 | 10.2.0.0/16
Creating the Subnets
Now we need to create subnets for the VPC's that we created. We will create the following subnets in our VPC, each subnet in its own availability zone:
10.1.0.0/20 (az-2a)
10.1.16.0/20 (az-2b)
10.1.32.0/20 (az-2c)
Let's go ahead and do this, head over to your green account, from the VPC section select "Subnets":
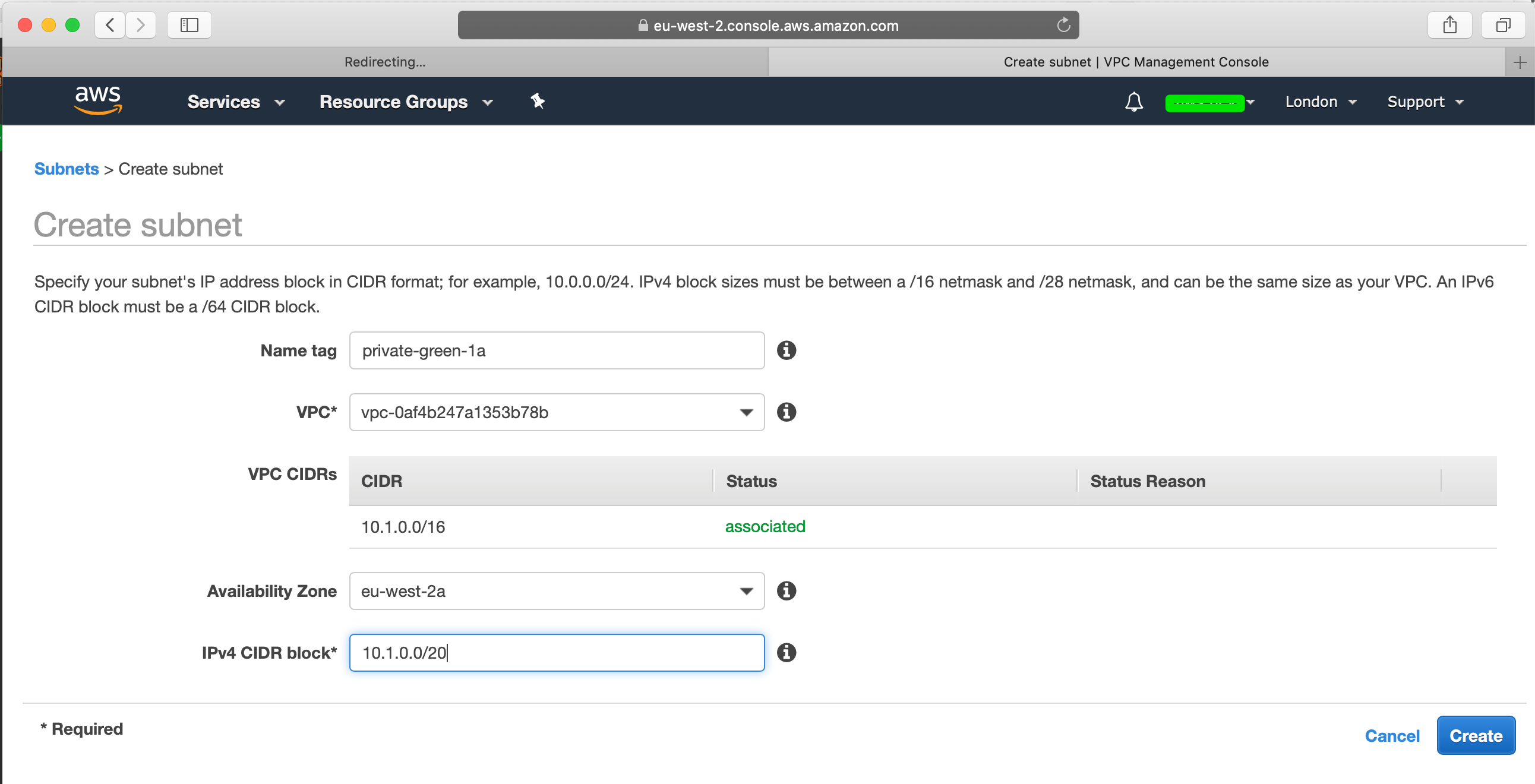
Go ahead and create a subnet where you will need to specify the VPC that you created, slect the first CIDR block, in my case 10.1.0.0/20 and select the first AZ:
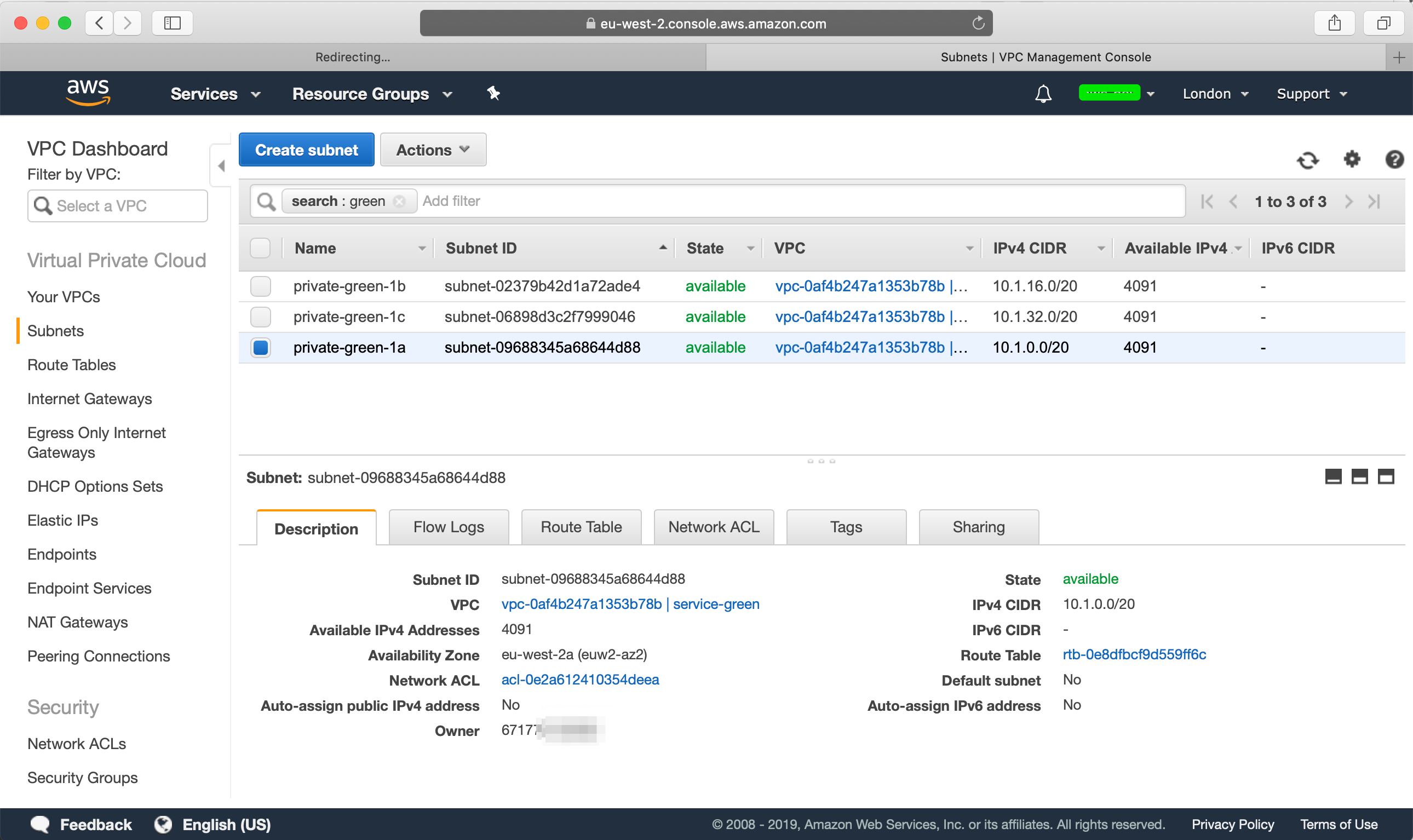
Do this for the other two subnets as well and then when you are done, it may look more or less like this:
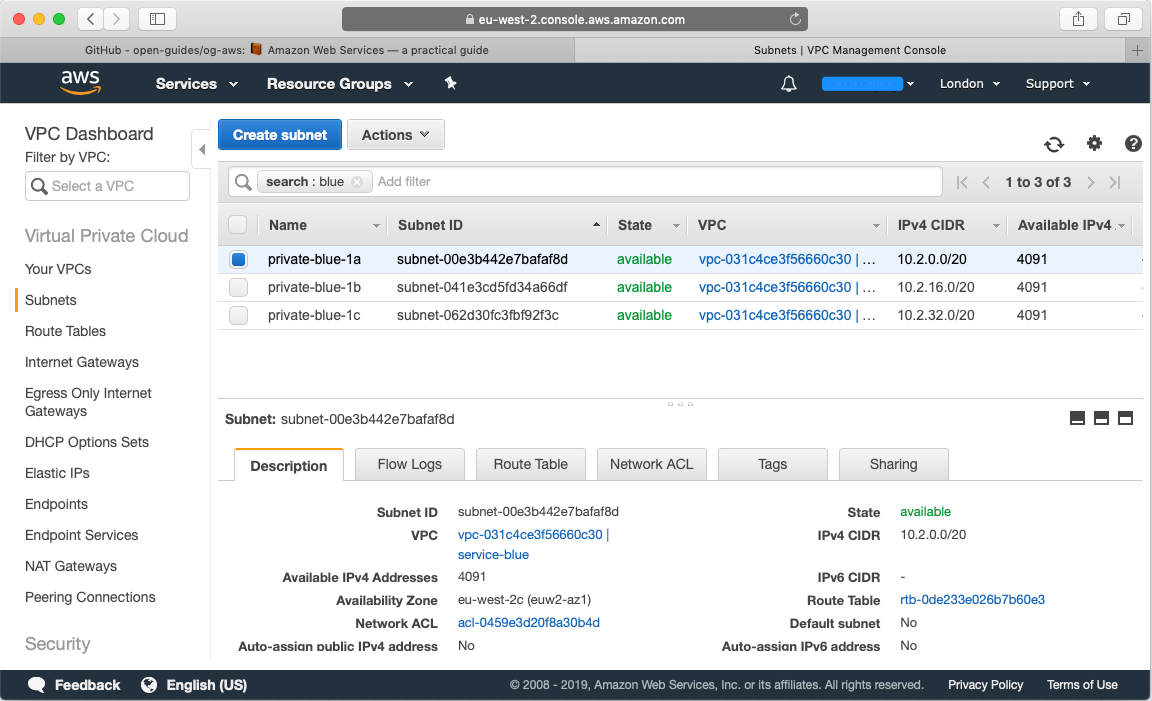
Repeat this process that you have three subnets for your blue account as well:
Setup VPC Peering Connection
Now that we've created our VPC's and subnets for each VPC we want to peer our two VPC's with each other so that we have a direct connection between our VPC's so that our EC2 instances from our green account is able to connect with our EC2 instances in our blue account.
Head over to your green account's VPC section and select "Peering Connections":
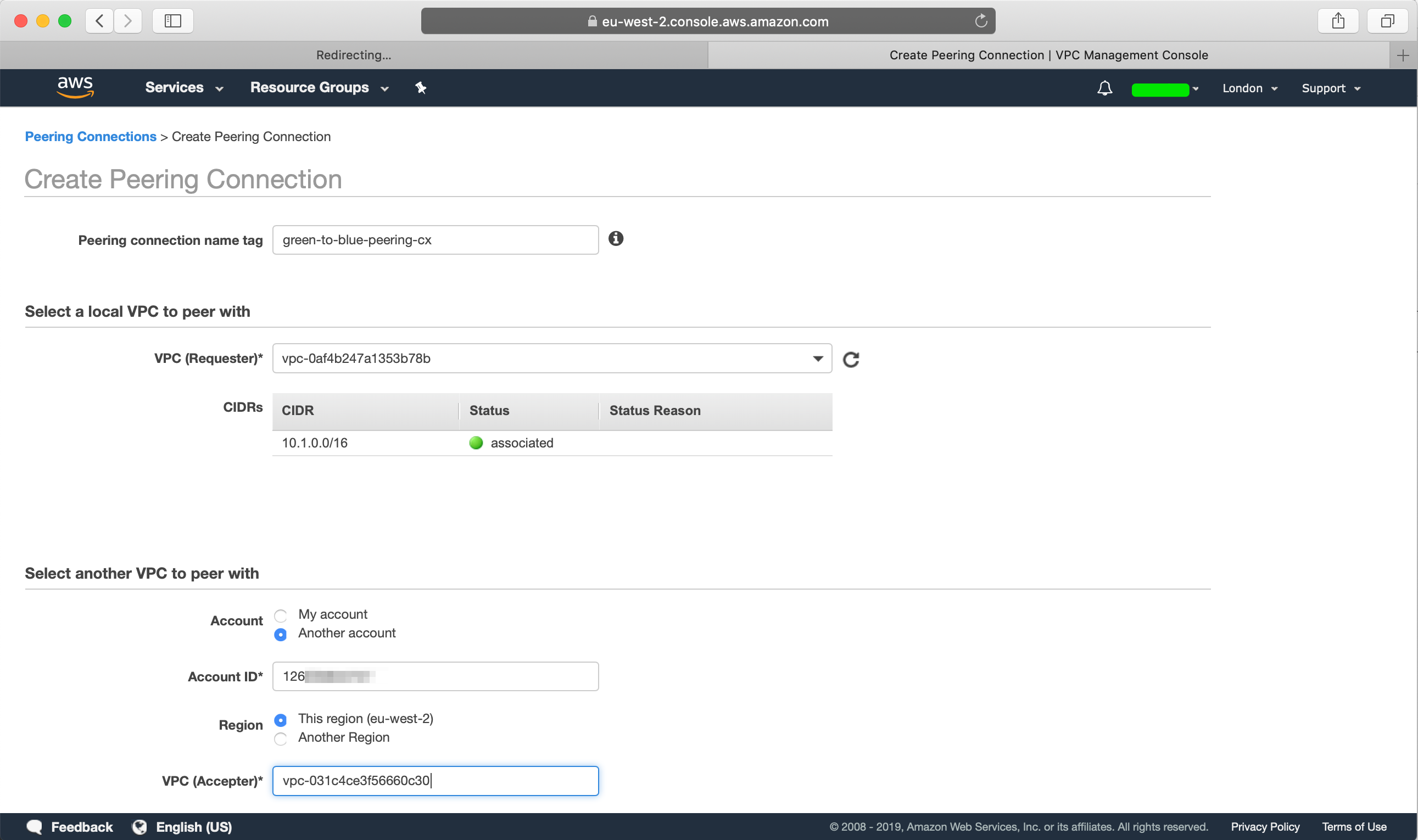
Create a new peering connection, we will first need to name our peering connection, select the source VPC which will be our green account's VPC, since the VPC that we want to peer with is in another account, get the AWS Account ID from the blue account, and select "Another account" and provide the account id that we want to peer with, select the AWS Region and provide the VPC ID of the blue account:
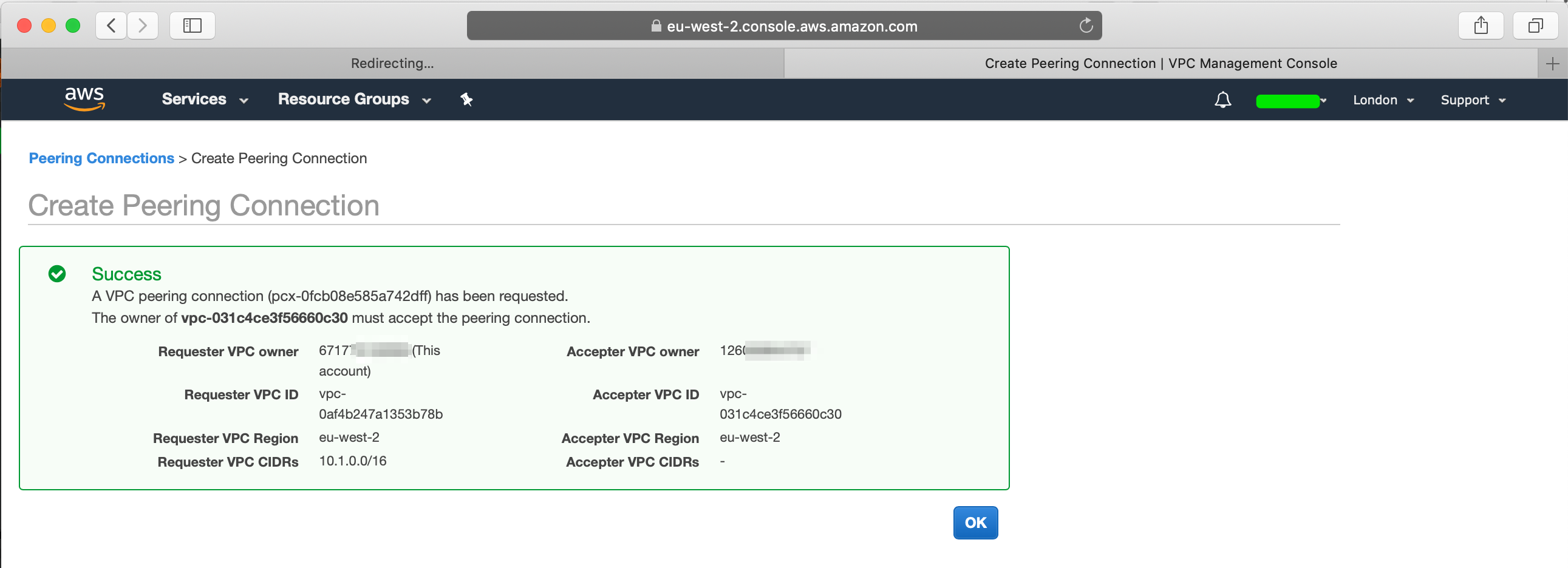
Once you create the peering connection, you will find the peering request details:
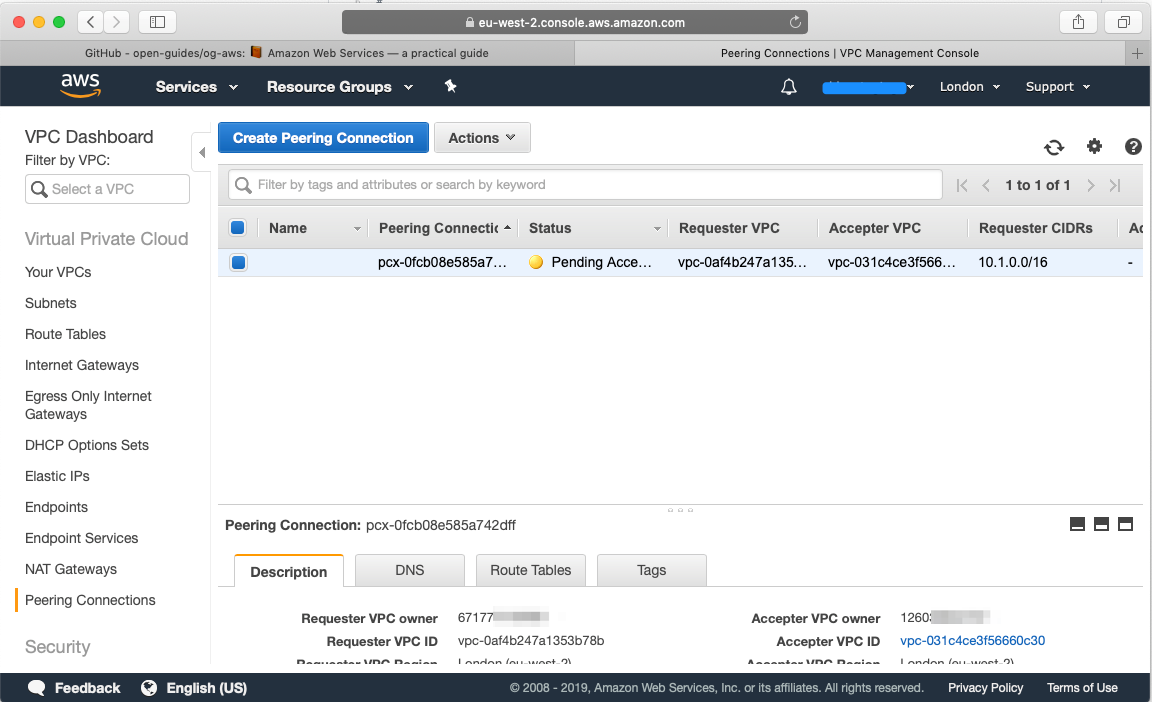
Now let's head over to our blue Account, head over to VPC, select Peering connections and you will find the peering request from our green account:
From the top, hit "Actions" and accept the request:
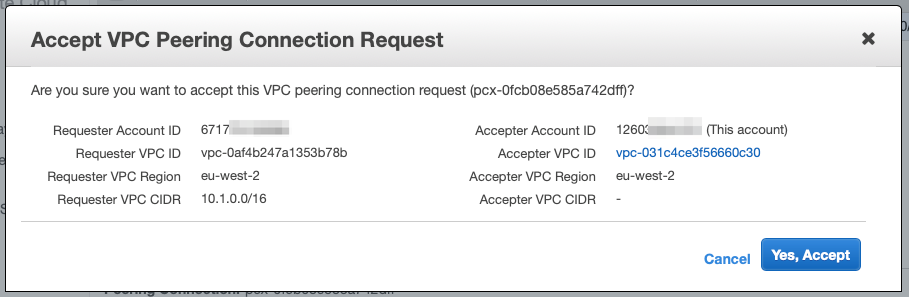
You should see that the VPC Peering connection has been established:
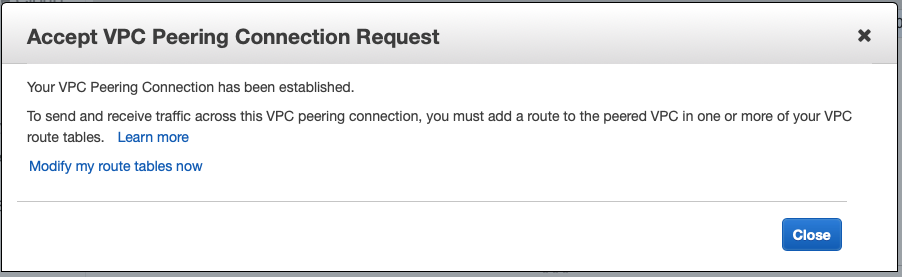
From the blue account you should see that the VPC Peering Connection is active:
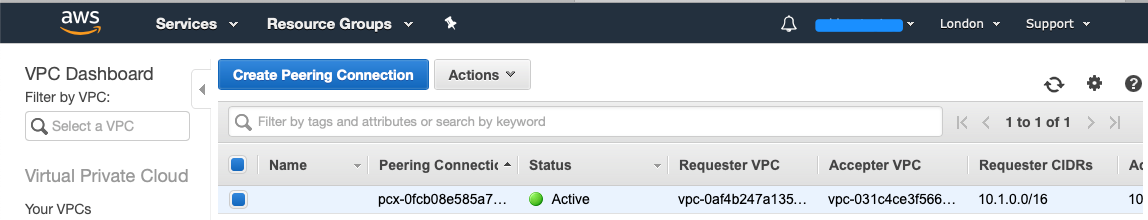
If you head back to the green account, you will see under Peering Connections that the connection has been established:
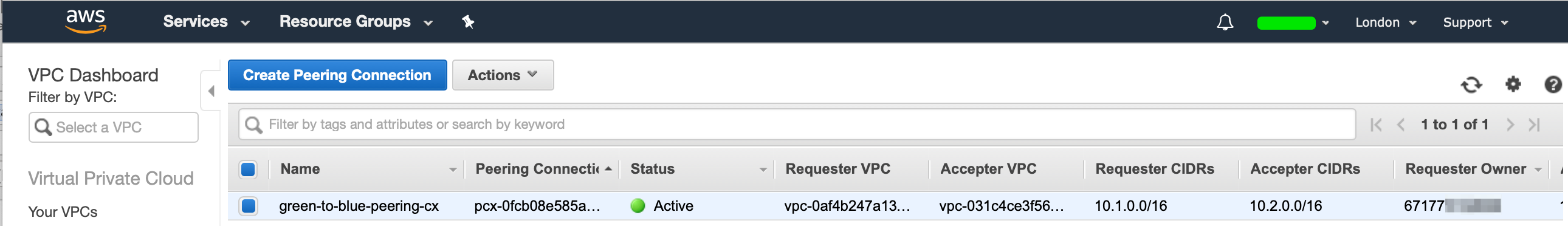
We have now successfully created our VPC peering connection and the two VPC's from different accounts has been peered. Now we would like to launch our EC2 instances in our VPC, we will connect to our EC2 instance in our green account via the internet and then SSH to our EC2 instance in our blue account via the VPC peering connection via the Private IP Address.
Setup Internet Gateway
In order to connect to a Public Elastic IP, we first need to create a Internet Gateway on our VPC and add a route to route all public traffic via our Internet Gateway. This allows our resources in that VPC to be able to connect to the Internet.
Head over to "Internet Gateways", and create a new Internet Gateway:
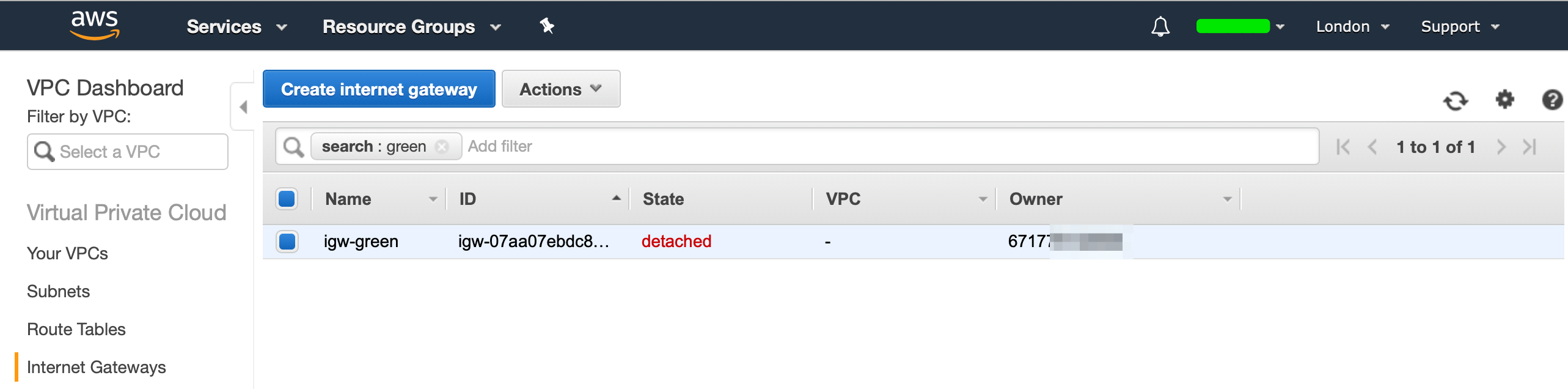
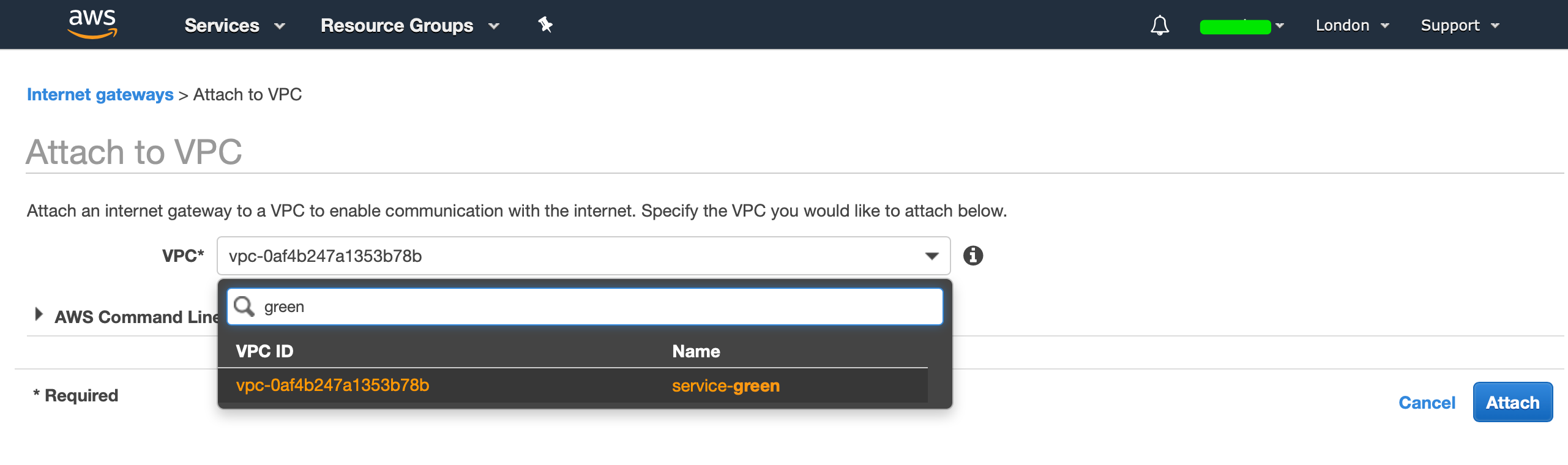
Our IGW (Internet Gateway) will now be in a detached state, we now need to attach our IGW to our VPC. Hit "Actions", then select "Attach to VPC", and select your VPC:
You should now see that your IGW has been attached to your VPC:
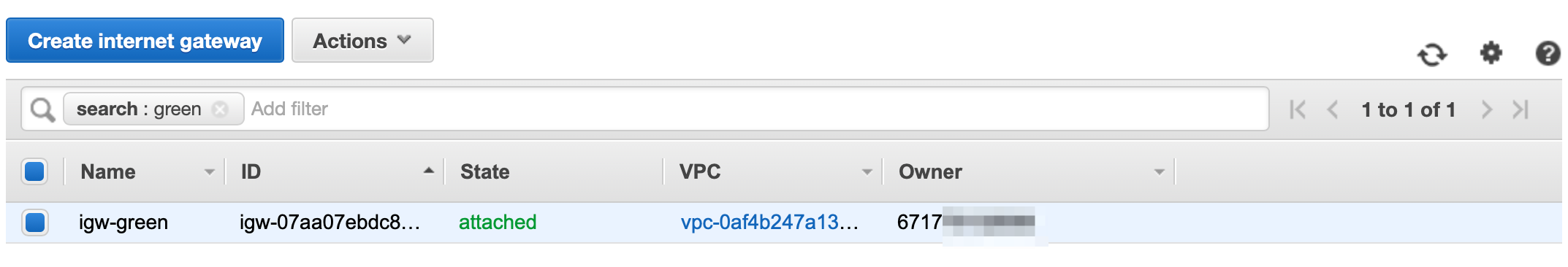
Now that we have created an IGW and associated it to our VPC, we now need to configure our routing table so that it knows how to route non-local traffic via the IGW.
Configure Routing Table
Head over to VPC, select your VPC, select the "Route Tables" section from the left and you should see the following when you select the "Routes" section:
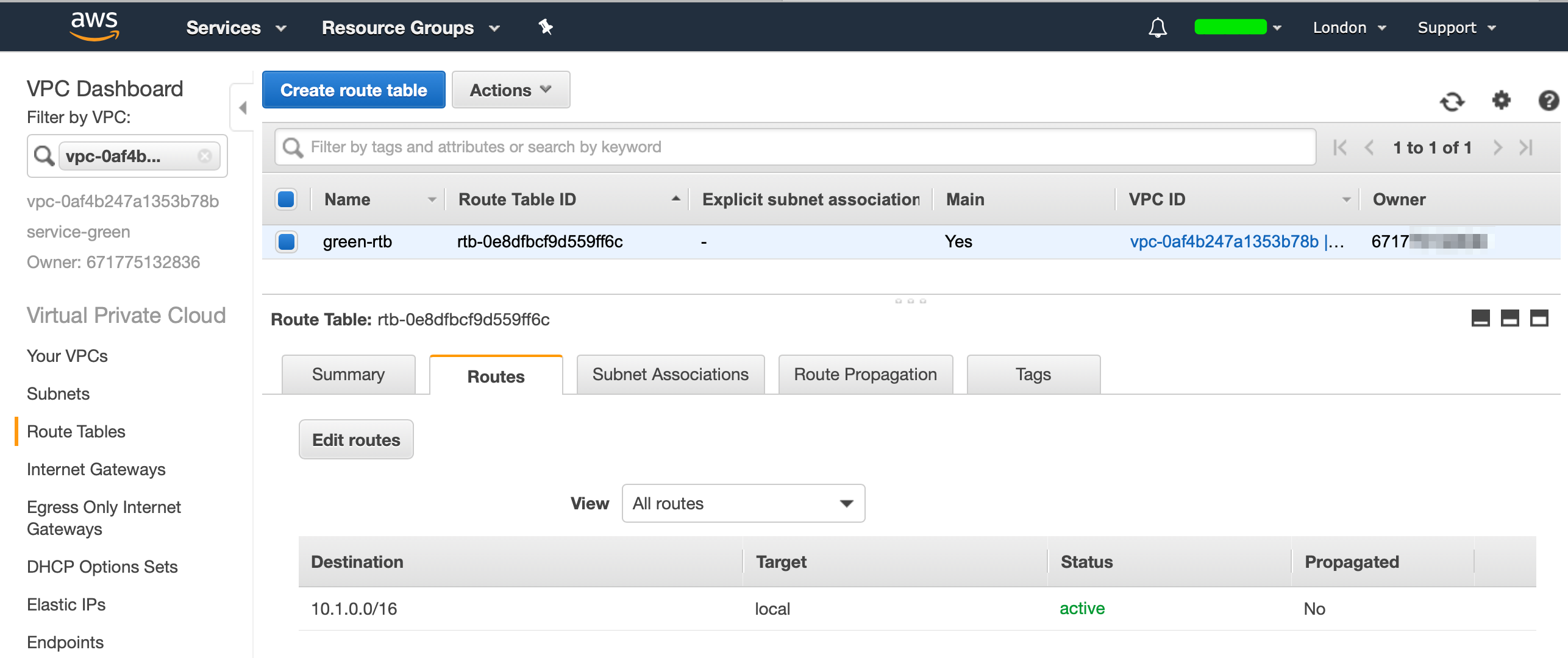
Select "Edit Routes" and add a route with the destination 0.0.0.0/0 select the Internet Gateway as a target and it will filter through your available IGW's and select the IGW that you created earlier, then select save. (If your blue account needs internet access, repeat these steps on the blue account as well.)
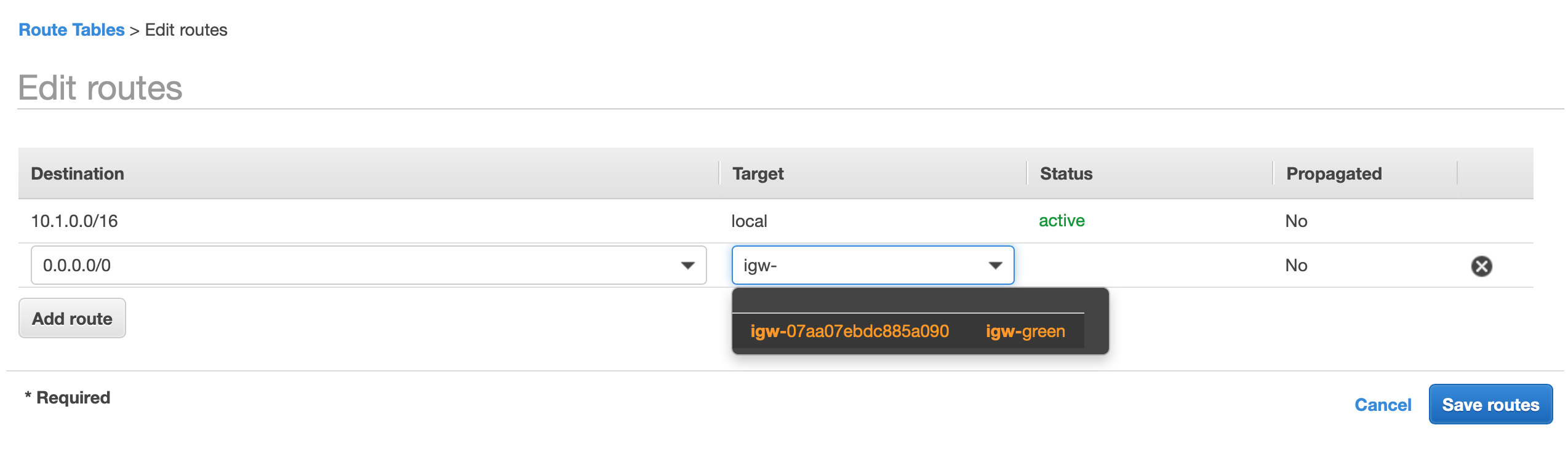
While we are at our routing tables configuration, we should also inform our VPC how to reach the subnet from the VPC from the other account. So that our Green App (10.1.0.0/16) can reach our blue app (10.2.0.0/16) via the Peering Connection.
We do this by adding a route to our routing table. From the green account's VPC's routing table add a new route with the destination of 10.2.0.0/16, select "Peering Connection" as the target and it should resolve to the peering connection resource that we created, then select save:
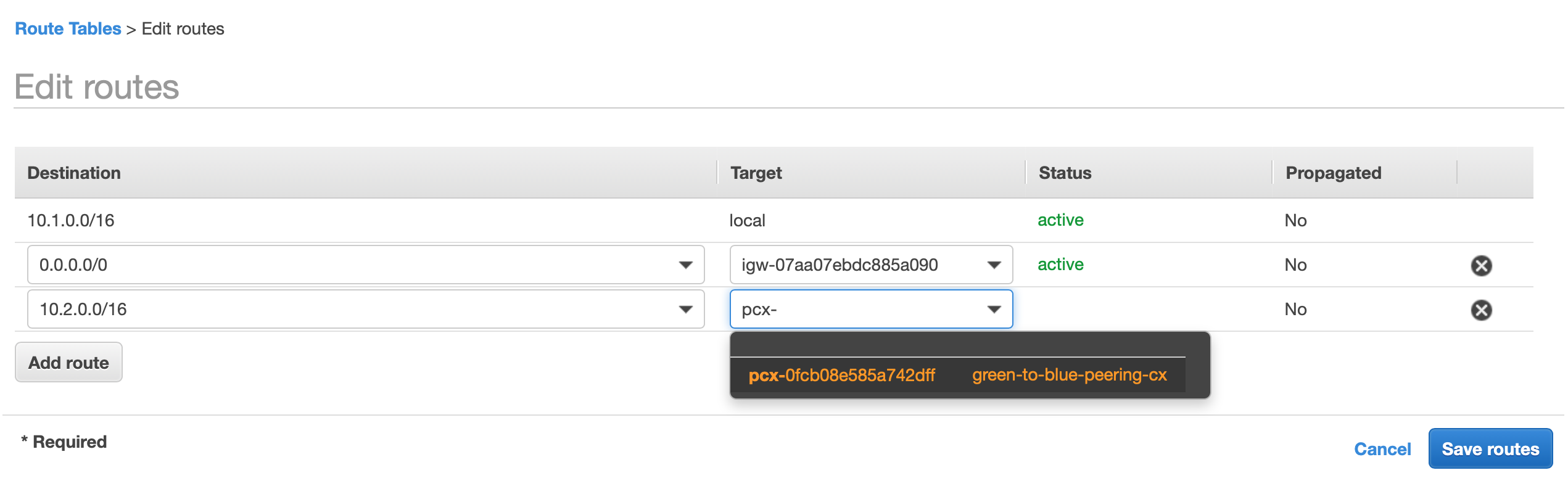
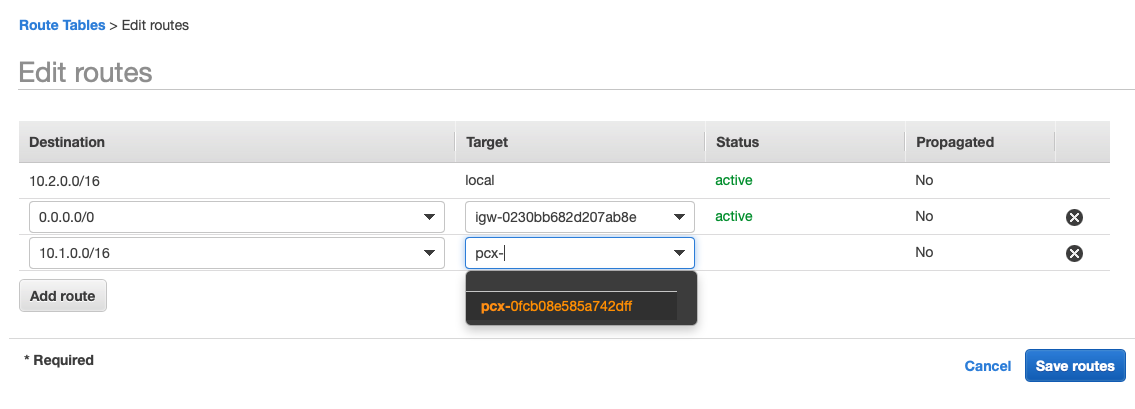
Now our green Account knows how to route traffic to our blue account and also knows which network traffic to route. But we also need to route traffic back. Head over to your blue Account and add a route 10.1.0.0/16 to the peering connection so that we can route traffic back to our green Account:
Launch EC2 Instances
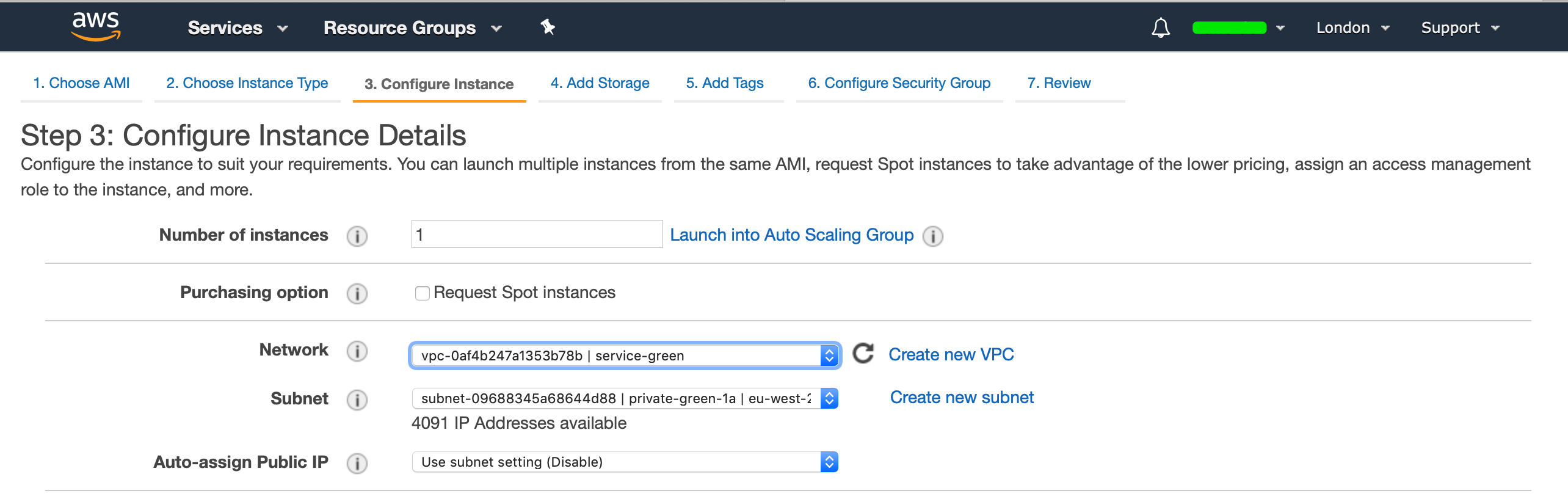
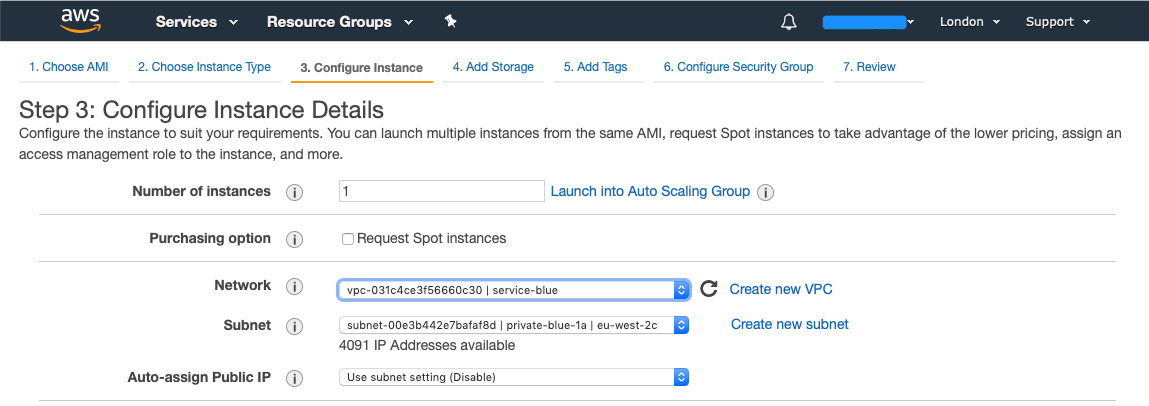
Now we want to launch a EC2 instance in each account and ensure to launch them into the VPC's that we created, I will also be creating two new SSH keys (blue-keypair + green-keypair) And I have created a Security Group that allows ICMP and SSH from anywhere, this is purely for demonstration (always review the sources that you want to allow).
For our green account:
For our blue account:
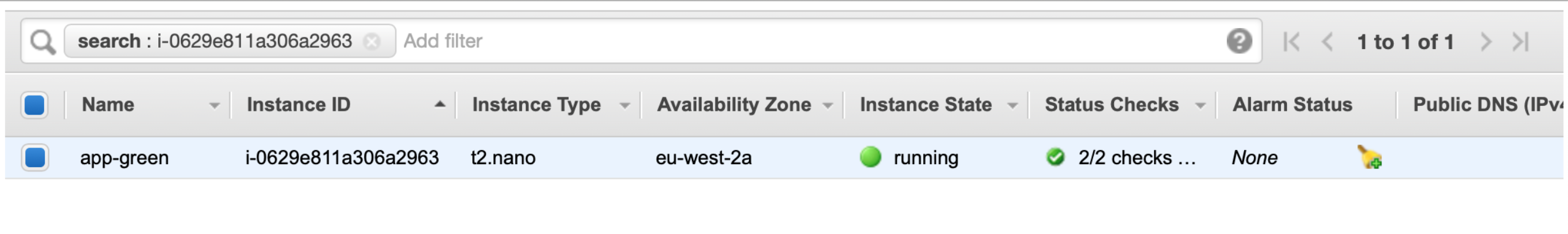
Once the EC2 instances are deployed, you should see something like this. For my green account:
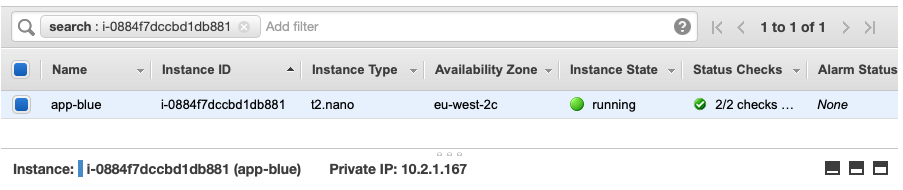
And for my blue account:
Public IP Addressing
Now that our EC2 instances are provisioned, we will be connecting to our green EC2 instances using a Public IP, therefore we need to create a Elastic IP. From EC2, select Elastic IPs and allocate a New Address:
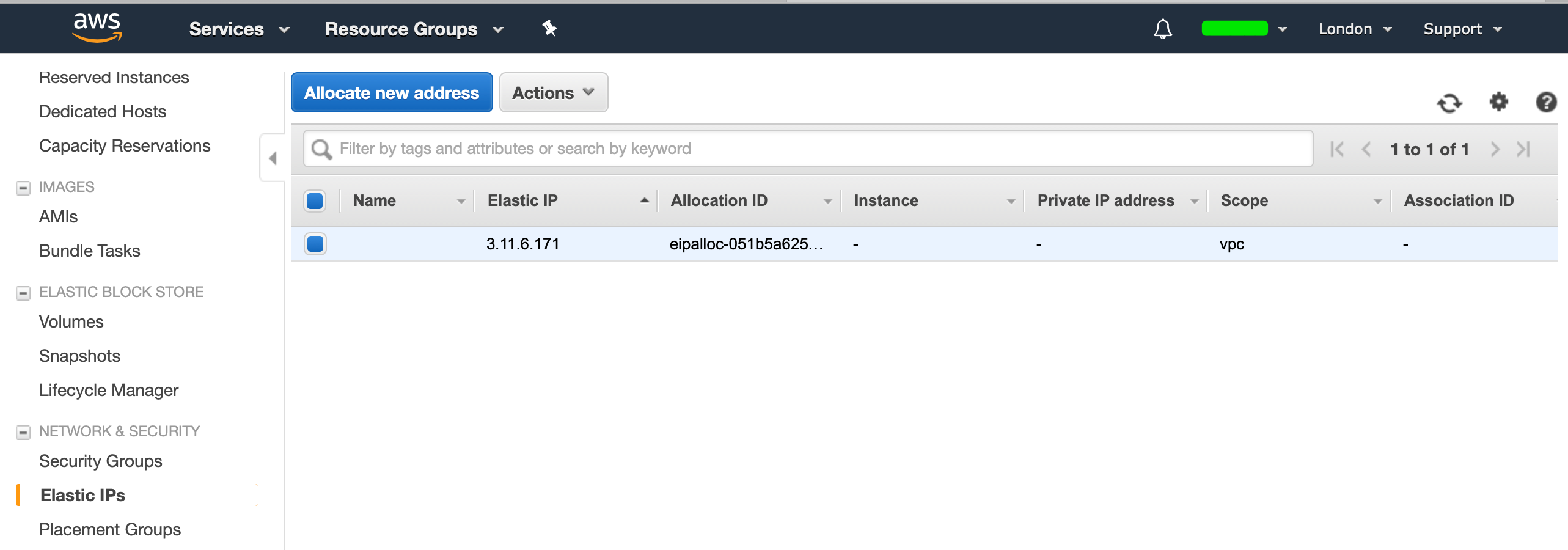
Select the IP, hit "Actions" and select "Associate Address", then select the EC2 instance to which you want to associate the Elastic IP to:
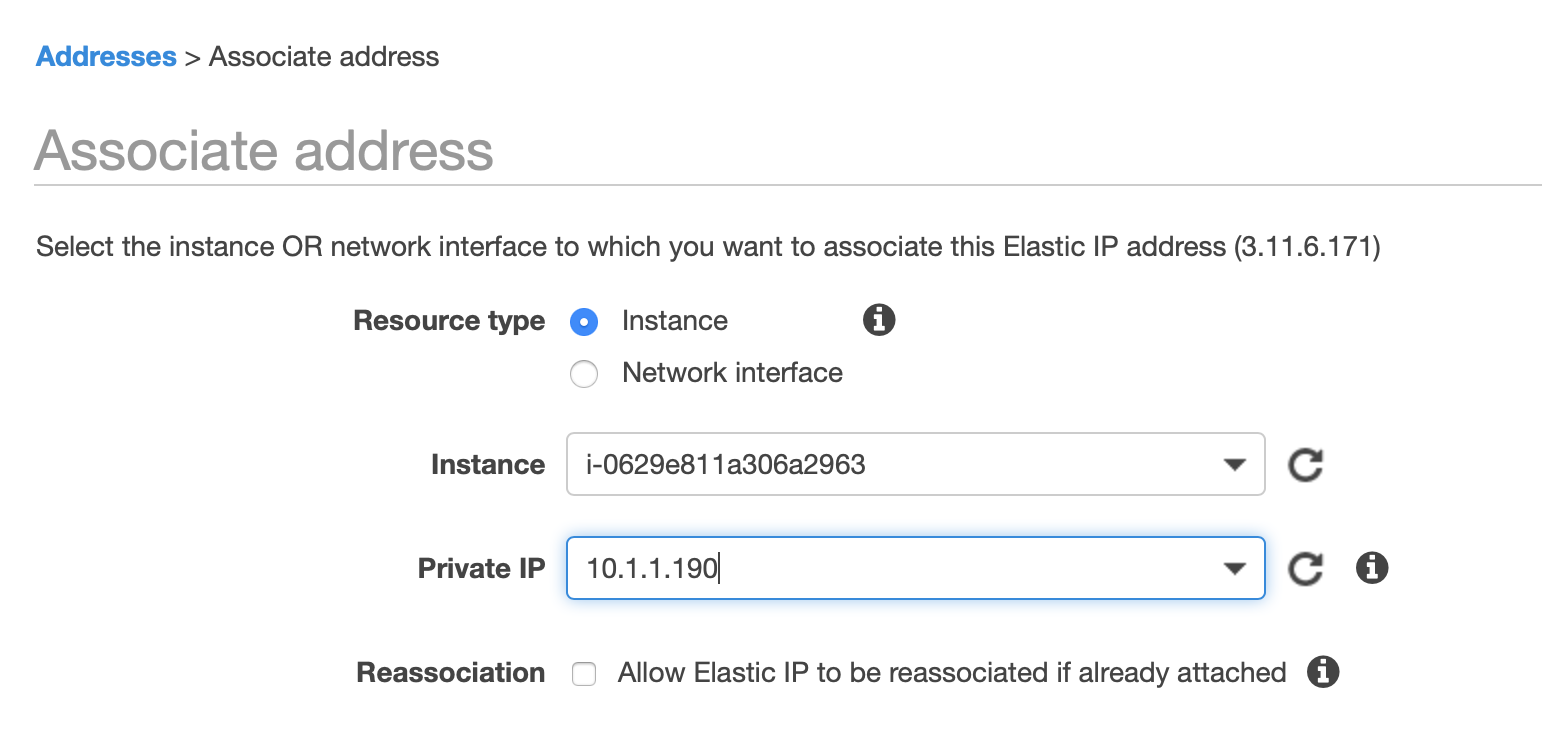
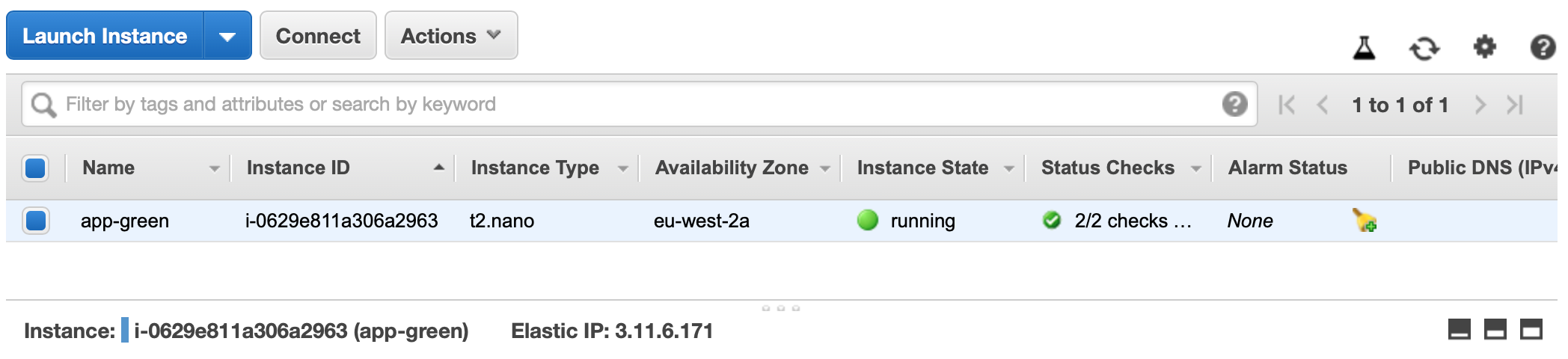
You should know see that the EC2 instance has a Public IP assigned to it:
Test Network Connectivity
From the downloaded SSH keypairs:
$ ls | grep keyp
blue-keypair.pem.txt
green-keypair.pem.txt
Apply the correct permissions to our keypairs so that we can use them to SSH:
$ chmod 0400 blue-keypair.pem.txt green-keypair.pem.txt
We will want to add both SSH keys to our agent so we can include them when we SSH:
$ eval $(ssh-agent -t 36000)
Agent pid 6613
Add both keys to your ssh-agent:
$ ssh-add blue-keypair.pem.txt
Identity added: blue-keypair.pem.txt (blue-keypair.pem.txt)
$ ssh-add green-keypair.pem.txt
Identity added: green-keypair.pem.txt (green-keypair.pem.txt)
SSH to our Green EC2 instance:
$ ssh -A ec2-user@3.11.6.171
__| __|_ )
_| ( / Amazon Linux 2 AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-2/
[ec2-user@ip-10-1-1-190 ~]$
Now lets ping our Blue EC2 Instance which will be accessible via our VPC Peering Connection:
[ec2-user@ip-10-1-1-190 ~]$ ping 10.2.1.167
PING 10.2.1.167 (10.2.1.167) 56(84) bytes of data.
64 bytes from 10.2.1.167: icmp_seq=1 ttl=255 time=0.754 ms
64 bytes from 10.2.1.167: icmp_seq=2 ttl=255 time=0.854 ms
And since we've allowed SSH traffic, we should be able to SSH to our instance via its Private IP Address:
[ec2-user@ip-10-1-1-190 ~]$ ssh 10.2.1.167
__| __|_ )
_| ( / Amazon Linux 2 AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-2/
[ec2-user@ip-10-2-1-167 ~]$
Now we have successfully created a VPC Peering Connection between Two AWS Accounts and demonstrated how to communicate to and from resources in those VPC's.
Thank You
Thanks for reading, if you like my content, feel free to check out my website, and subscribe to my newsletter or follow me at @ruanbekker on Twitter.
- Linktree: https://go.ruan.dev/links
- Patreon: https://go.ruan.dev/patreon




